Importação (Baixa→Alta)
- Evita que o malware entre em redes classificadas.
- Combina Multiscanning, Adaptive Sandbox Analysis, Deep CDR, controlo unidirecional e quebras de protocolo.
Permita a colaboração de missão crítica com as soluções modulares e específicas da OPSWAT.
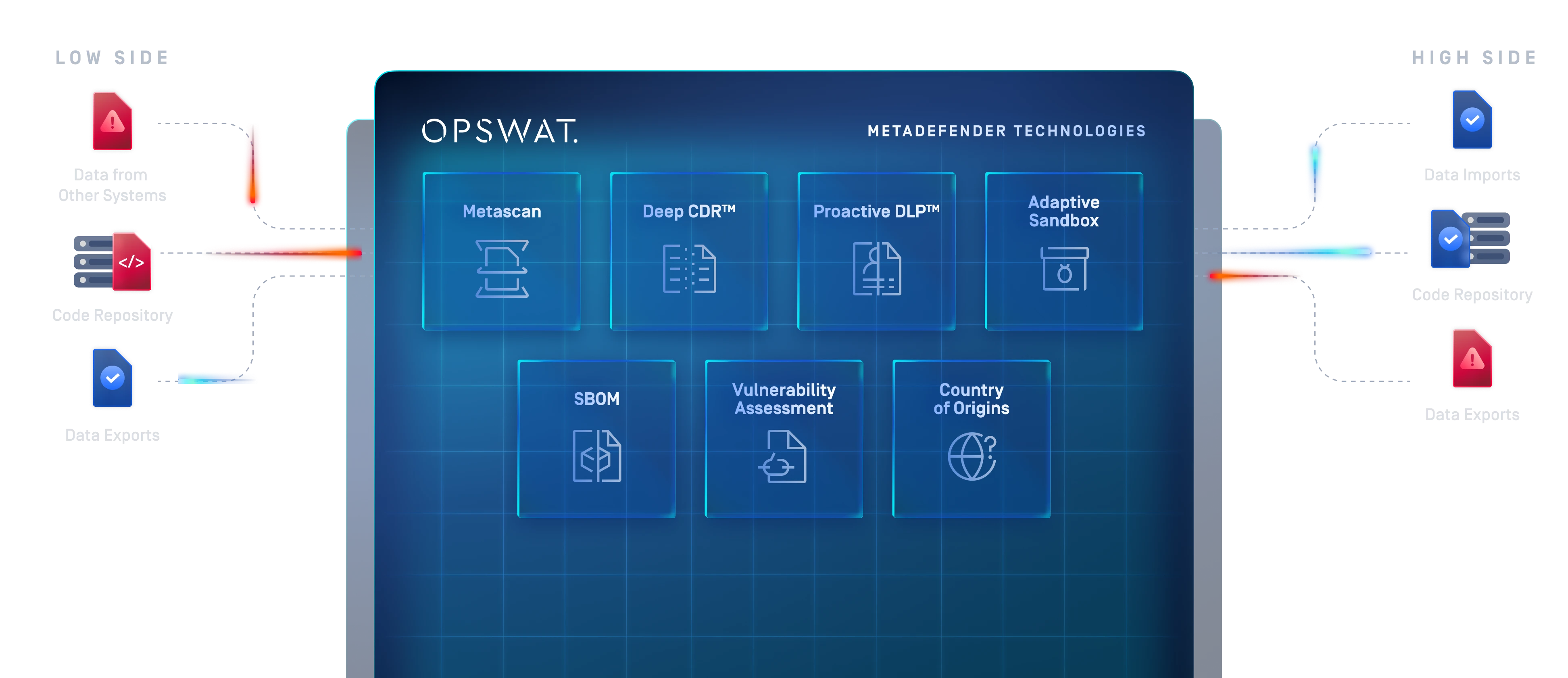


Os dados que se deslocam entre domínios são agora apresentados em grandes volumes e em diversos formatos, desde ficheiros do utilizador diário a dados geoespaciais, instaladores e actualizações de aplicações. Os sistemas legados e apenas de hardware têm dificuldade em processar esta variedade e não podem ser dimensionados para fornecer as Funções de Execução de Segurança (SEFs) necessárias de uma forma flexível e expansível.


Os sistemas têm de resistir a atacantes com muitos recursos, incluindo ameaças de estados-nação. As transferências de dados entre níveis de segurança expõem vulnerabilidades que as defesas tradicionais não conseguem resolver, enquanto os ataques impulsionados pela IA exigem uma proteção moderna e adaptável.


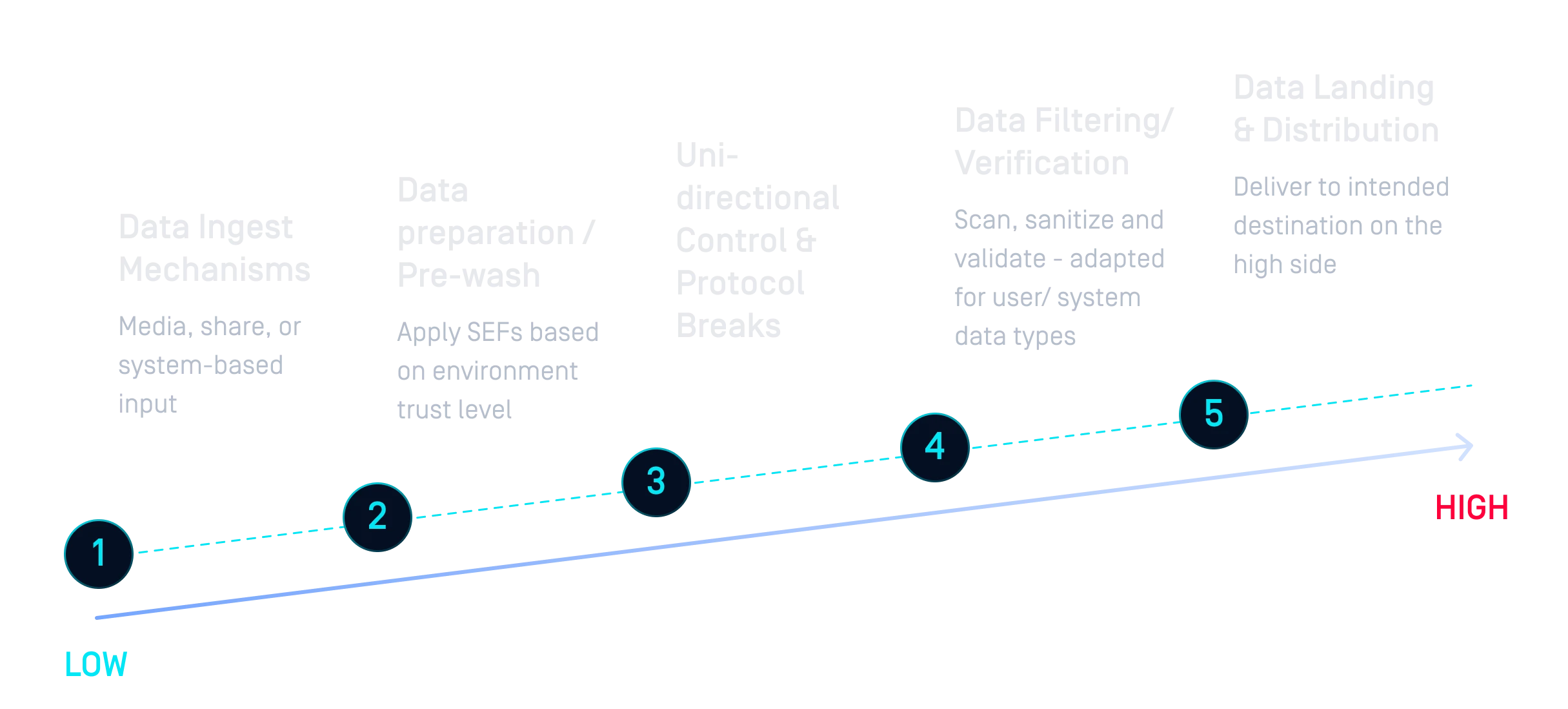
O isolamento permanente dos dados não atende mais às necessidades de colaboração entre territórios. Os sistemas CDS modernos devem se adaptar às demandas de negócios, suportando diversos volumes, tipos de dados e aplicativos, permitindo transferências contínuas APIAPI e de nuvem para local.
OPSWAT fornece uma abordagem modular, baseada em software, que acrescenta aos processos existentes,
com tecnologias líderes de mercado.
Com tecnologias líderes de mercado e capacidades plug-in/plug-out, a abordagem modular da OPSWATé uma forma mais eficiente de construir soluções CDS.
Com a sandbox de emulação, as organizações podem analisar os IOCs em tipos de dados complexos, como patches de SO ou aplicações, e eliminar potenciais vectores de ameaça.
Proactive DLP pode ajudar a garantir que os dados transferidos de classificações mais elevadas para classificações mais baixas (como relatórios partilhados com parceiros) não contêm informações sensíveis, não destinadas a serem divulgadas, detectando-as e bloqueando-as nos ficheiros.
Com o MetaDefender Kiosk, os dados provenientes de Media amovíveis podem passar pelos mecanismos de aplicação de segurança que são apropriados com base na postura de risco da sua organização.
Uma das principais vantagens é que a utilização do MD Core em conjunto com ferramentas como MFT permite um rasto de auditoria completo, permitindo às organizações rastrear e ver que função ou pessoa tentou exfiltrar os dados.
Ao contrário das abordagens tradicionais com air-gap que isolam os dados e dificultam a colaboração, as soluções da OPSWATintegram-se em arquitecturas de vários domínios e aplicam políticas de segurança. A abordagem híbrida de hardware-software suporta várias comunidades de interesse, assegurando simultaneamente que os dados sensíveis são devidamente controlados, monitorizados e auditados.
À medida que os ciberataques e os agentes de ameaças que os executam se tornam mais sofisticados, os organismos governamentais de todo o mundo estão a implementar regulamentos para garantir que as infra-estruturas críticas estão a fazer o que é necessário para se manterem seguras.